
This class contains families specifying requirements for TOE security functions and TOE security function policies related to protecting user data. FDP is split into four groups of families (listed below) that address user data within a TOE, during import, export, and storage as well as security attributes directly related to user data.
The families in this class are organised into four groups:
a) User data protection security function policies:
- FDP_ACC Access control policy; and
- FDP_IFC Information flow control policy .
Components in these families permit the PP/ST author to name the user data protection security function policies and define the scope of control of the policy, necessary to address the security objectives. The names of these policies are meant to be used throughout the remainder of the functional components that have an operation that calls for an assignment or selection of an "access control SFP" or an "information flow control SFP". The rules that define the functionality of the named access control and information flow control SFPs will be defined in the FDP_ACF Access control functions and FDP_IFF Information flow control functions families (respectively).
b) Forms of user data protection:
- FDP_ACF Access control functions;
- FDP_IFF Information flow control functions;
- FDP_ITT Internal TOE transfer;
- FDP_RIP Residual information protection;
- FDP_ROL Rollback; and
- FDP_SDI Stored data integrity .
c) Off-line storage, import and export:
- FDP_DAU Data authentication;
- FDP_ETC Export to outside TSF control; and
- FDP_ITC Import from outside TSF control.
Components in these families address the trustworthy transfer into or out of the TSC.
d) Inter-TSF communication:
- FDP_UCT Inter-TSF user data confidentiality transfer protection; and
- FDP_UIT Inter-TSF user data integrity transfer protection.
Components in these families address communication between the TSF of the TOE and another Trusted IT Product.
Figure 6.1 and 6.2 show the decomposition of this class into its constituent components.
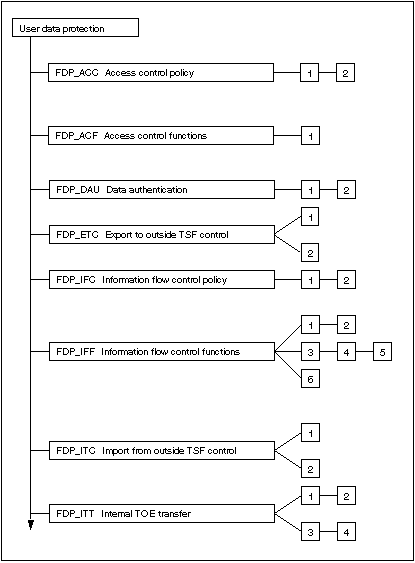
Figure 6.1 - User data protection class decomposition
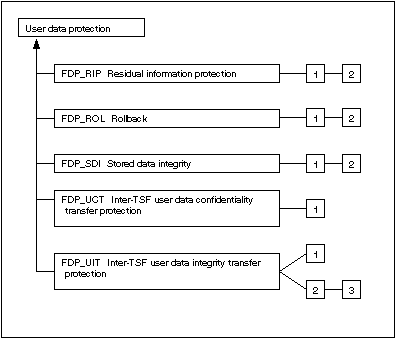
Figure 6.2 - User data protection class decomposition (cont.)